Did You Get Phished via Google Docs?
Do you use Google Docs?
Well, who doesn’t?
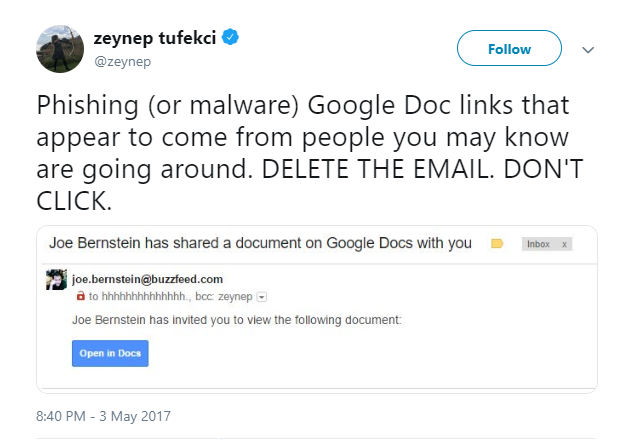
A few days ago you may have unsuspectingly clicked an invitation to edit a doc, sent to you by a trustful contact from your list.
Except that it wasn’t really a contact of yours, but a phishing scam that targeted many of approximately 1 billion Google users across the world. (According to Google, less than 0.1 percent of Gmail users, that is roughly 1 million people, actually bought into this trick.)
If it were only for the people who received the message, the damage wouldn’t be all that severe. But if you clicked on the link to the supposed document, your Gmail account got compromised, with the phishing email replicated and sent to all of your contacts.
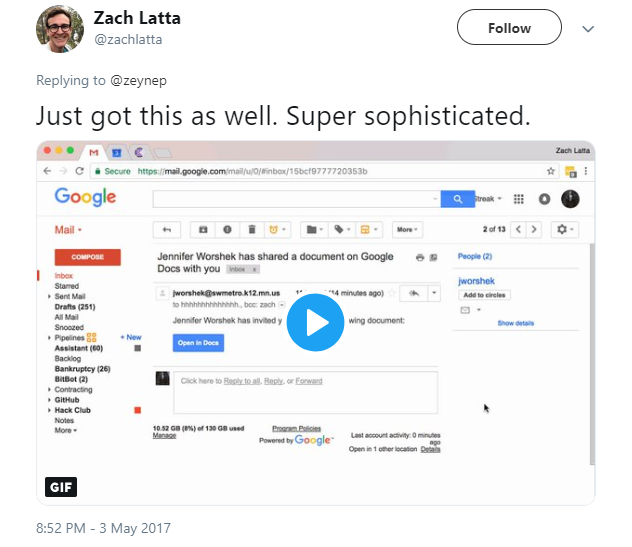
The most insidious thing about phishing attacks is that they (at least the best of them) are really good at disguising as trustworthy sources. Even the email address of the sender may seem to be completely valid, as it was the case with this attack as well.
In this case, there were two ways to determine something wasn’t right.
After clicking the bogus link, the user was redirected to a fake Google Docs which would then ask for access permission, not even falling for the two-factor authentication. Of course, the real Google Docs never asks for permission once you are logged in to your email account.
But then, how many people actually pay attention to all of the permissions apps require or don’t require from us?
The second detail that could have ringed the bell was the “To” field. It read hhhhhhhhhhhhhhhh@mailinator.com, whereas the actual user’s address was in the BCC field.
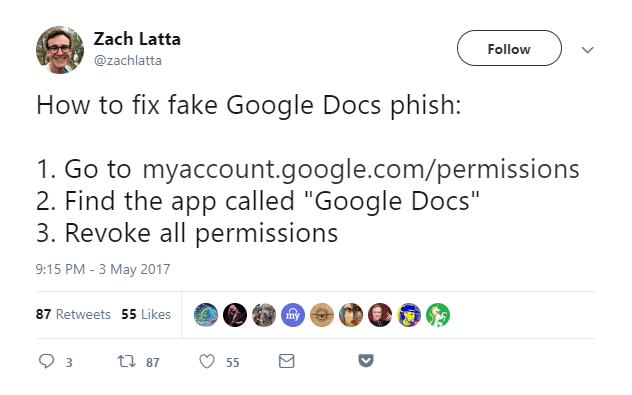
Steps to remedy are super simple.
But the problem doesn’t cease to exist altogether once you do this. The attacker doesn’t have access to your account anymore, but they still have all of your information neatly stored on their servers.
Google was fast to discover this threat, and even faster to fix it by disabling the dreaded app. “We were able to stop the campaign within approximately one hour. While contact information was accessed and used by the campaign, our investigations show that no other data was exposed. There’s no further action users need to take regarding this event; users who want to review third party apps connected to their account can visit Google Security Checkup,” they announced.
Phishers don’t give up on Google (and everything else)
A few months ago there was another subtle phishing attack that targeted Gmail users and managed to trick even the tech-savvy and cautious ones. Users received emails from their supposed contacts, which looked completely legit. An attachment that looked like a known image would then lead them to a spurious page identical to the Google sign-in page, which would collect their credentials.
The new Chrome update labeled this sign-in page Not Secure, thus warning the users that any further action would be unwise.
Recently there was one more perfidious phishing attack. This time it didn’t execute via email, but via the URLs of well-known websites, which got spoofed by a homograph attack. This was a masterful attack because a naked eye could never spot the difference between legit and fake URL.
Phishing scams are growing in volume and subtlety. Suspicious minds will sometimes manage to avoid trouble, while wasting terrible amounts of time by double-checking EVERY possible detail in EVERY email they receive during a busy workday.
But sometimes even paying attention won’t help.