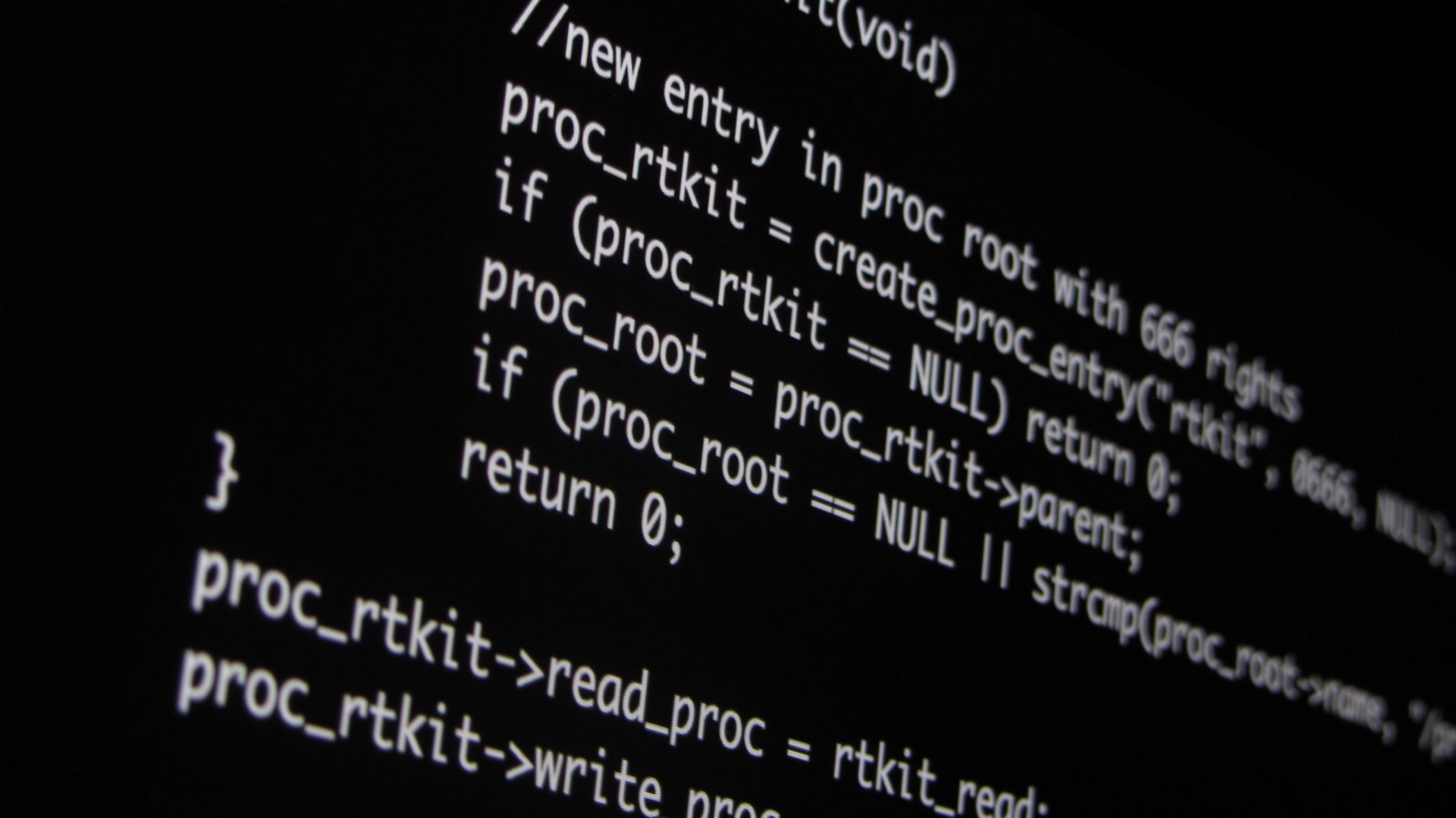
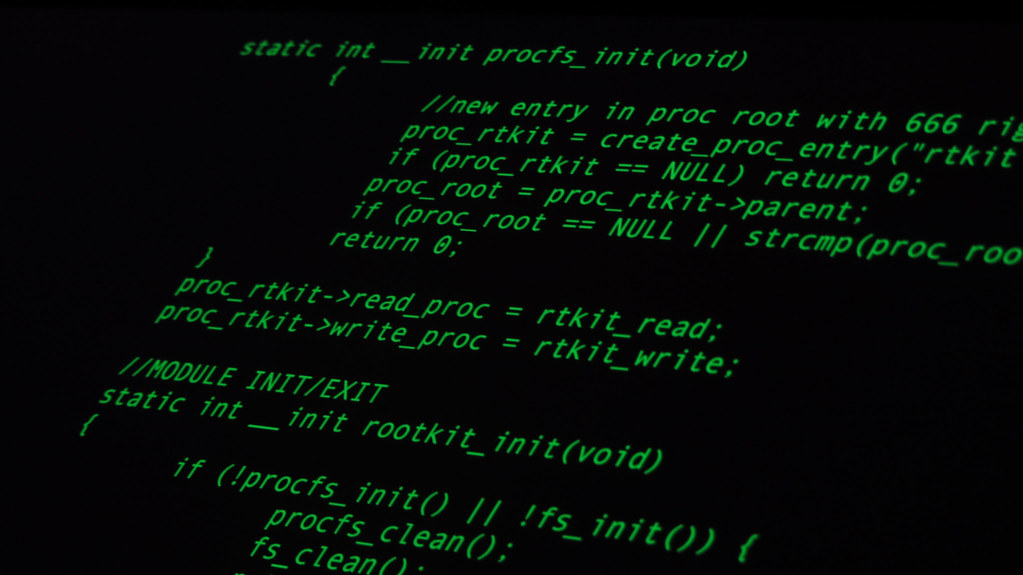
How Internet Access Affects Income
The lack of universal and affordable access to the internet may widen income inequality within and between countries, a senior official of the International Monetary Fund (IMF) has said while urging policymakers to foster a digital-friendly business and regulatory environment.