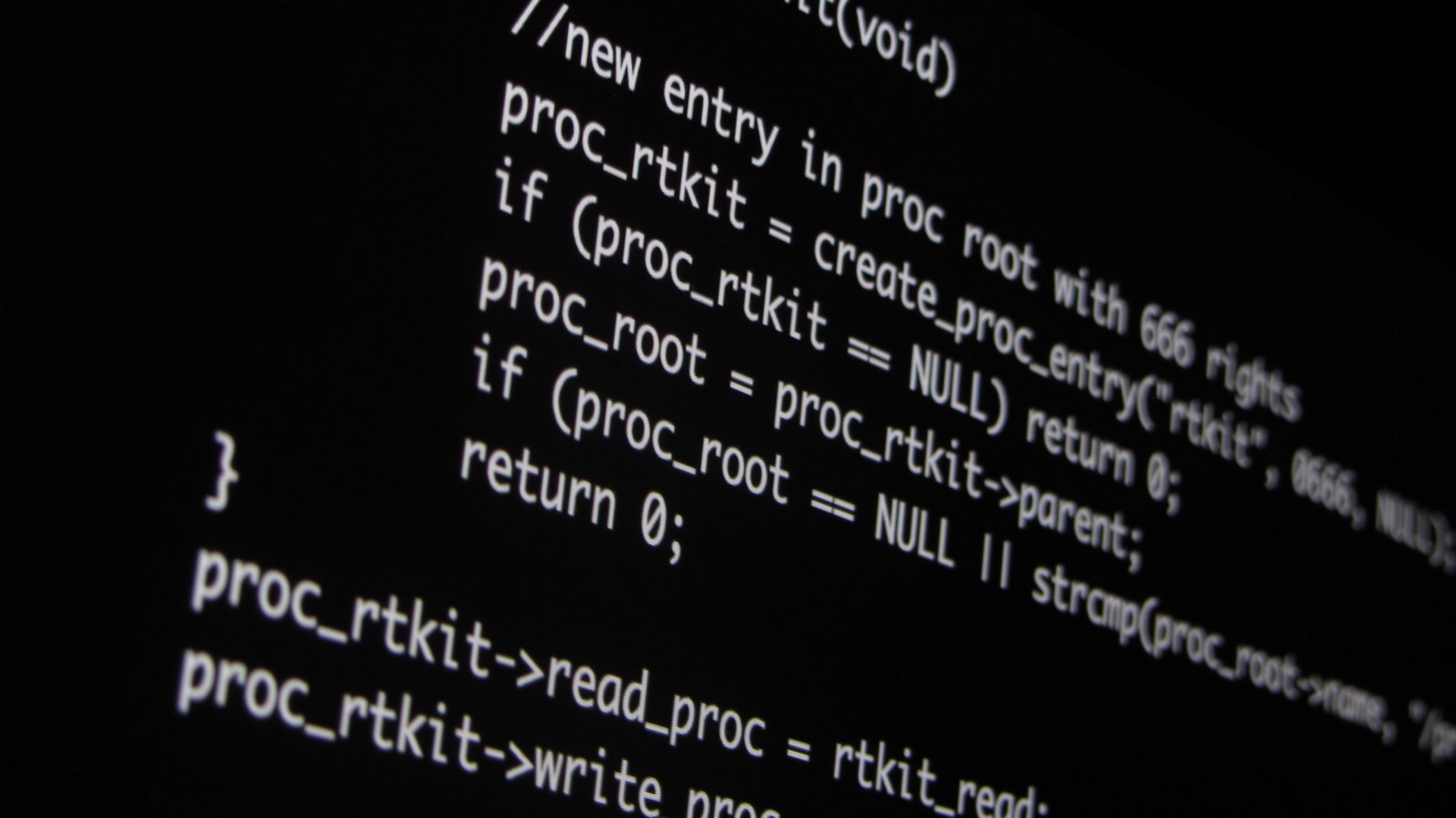
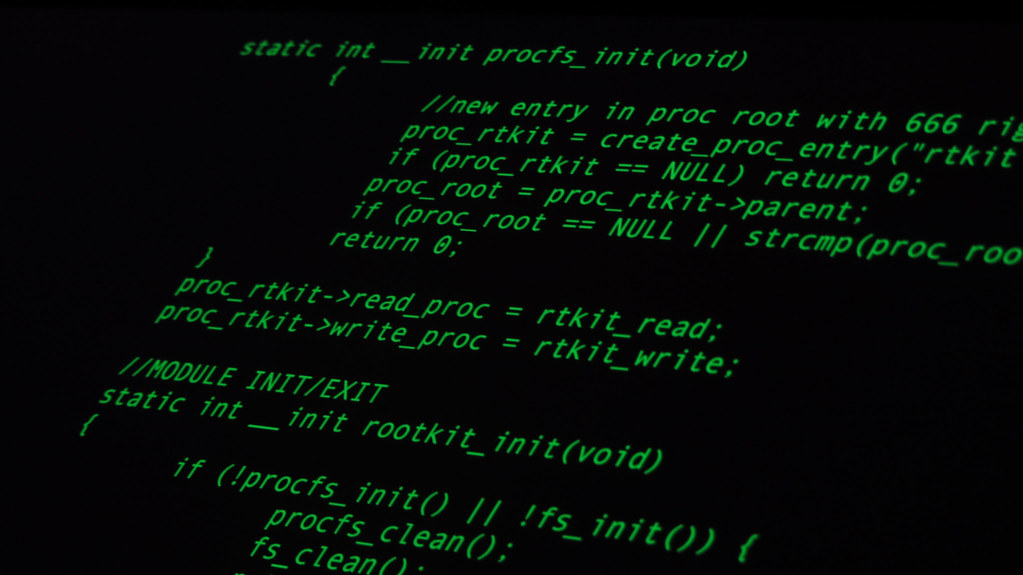
How to Prevent a Rootkit Attack
Rootkit attacks are dangerous and harmful, but they only infect your computer if you somehow launched the malicious software that carries the rootkit. The tips below outline the basic steps you should follow to prevent rootkit infection.