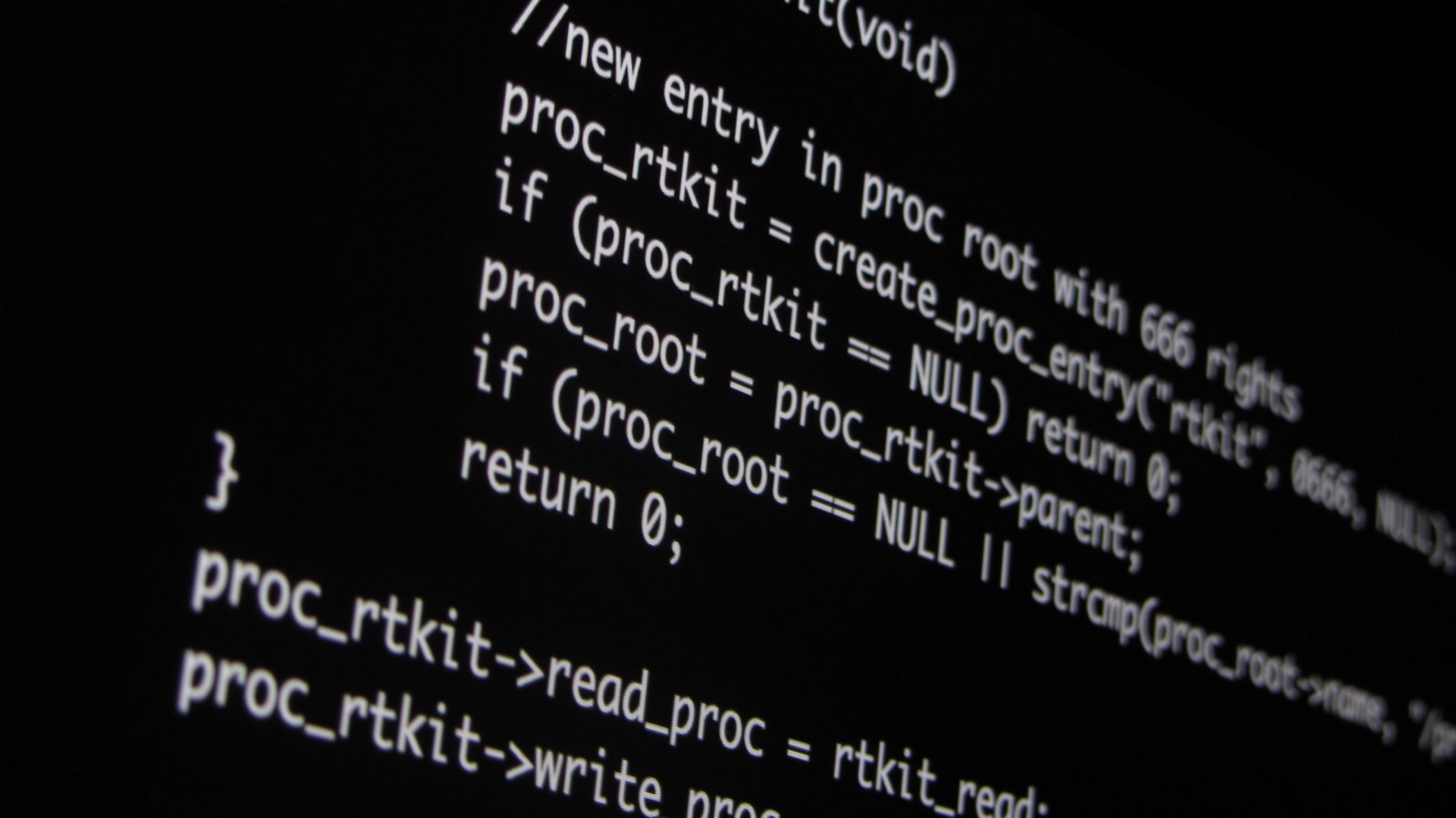
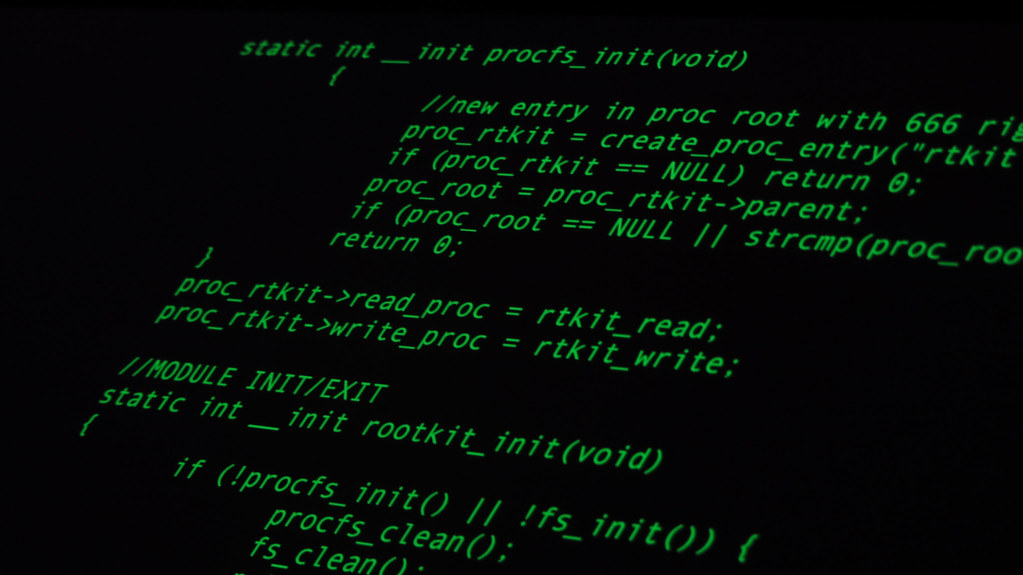
Cyber Security Is Rarely Considered When Buying IoT Devices
In today’s often-precarious security and privacy landscape, you’d think consumers would be taking security and privacy risks into serious consideration when purchasing new IoT devices. And you’d be wrong.