Internet of Things: The Quiet Threat from the Inside
Internet of Things is increasingly infiltrating our lives not only at work, but also in our homes with people continuing to buy and install all kinds of smart devices in their houses. Yes, it is handy to have a device open you the front door because it has somehow recognized that your hands are full, and more importantly – that it is in fact you coming up. However, as per usual, the less money, skill and preparation you invest in the devices and building your IoT network, the more problems you can expect down the line.
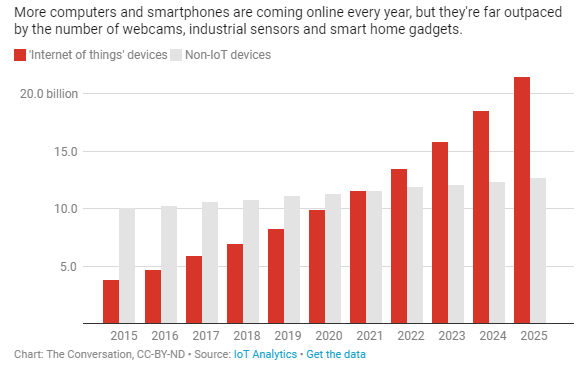
The ever-expanding number of sensors and remote monitors is due to companies’ use in managing overhead lights in corporate offices and manufacturing processes in factories. Moreover, cities governments and municipalities are willing to use new smart tech in their quest to improve energy efficiency and water quality and reduce traffic congestion. Hence, the number of IoT devices has climbed into the tens of billions creating an interconnected world where people’s lives are more productive, enjoyable, efficient and secure. But HOW SECURE is the main question. These devices have very sparse security protections which can make them part of botnets – and thus open to being hijacked by hackers.
Botnets are famous for causing problems on the Internet, from sending vast amounts of spam mail to disrupting websites around the world. While traditionally most botnets are comprised of laptop and desktop computers, the growth of unsecured devices such as industrial sensors, webcams, televisions and other smart home devices is leading to a growing disruptive capability.
The Internet of Things includes countless types of devices – webcams, pressure sensors, thermometers, microphones, speakers, stuffed animals and many more – made by a vast array of companies. Many of these manufacturers are small and unknown and don’t have popular brands or public reputations to protect by particularly investing in security measures. Their goal is to produce a lot of devices that they will be able to sell as cheaply as possible afterward. Thus, customers’ cybersecurity isn’t a real concern for them.
The variety of these devices means they’re useful for numerous things, but also means they have a wide range of vulnerabilities such as weak passwords, unencrypted communications and insecure web interfaces. With hundreds of thousands of identically insecure devices worldwide, they’re a wealth of targets for those who are looking to explore them.
If, for instance, a manufacturer has set an unchangeable administrative password on a particular type of device, which is a pretty common occurrence, a hacker can find such devices, log in, take control and install their own malicious software, thus taking over the device for their own use. The devices run normally until the hackers issue instructions, after which they can do more or less anything a computer might do – such as sending meaningless internet traffic to clog up data connections.
That type of attack when coming from thousands of devices at once – distributed denial of service – can shut down company servers or even block big blocks of the Internet from being publicly accessible. The size and scale of these attacks – and the broad range of devices that can contribute to them – make this both a private problem and a public one. People want to secure the devices in their homes and pockets, of course. Yet the same networks that stream television shows and music also link burglar alarms to police, manage traffic lights in congested areas and let self-driving cars talk to each other.
All that activity can be drowned out if hackers flood the internet, or sections of it, with meaningless messages. Traffic would stall across towns, even counties, and police officers would have a hard time communicating with each other to try to straighten everything out. Even small devices, in their hundreds of thousands, all around the world, can work together to have huge repercussions both online and in the physical world.
Therefore, cyber security starts with each individual user’s responsible behavior in cyber space. Understanding that each entity of the system is responsible for their actions because they influence all the other social participants is just the first step toward making it a safe environment for both individuals and organizations.