8 Most Common Cyber Security Threats
Nearly every networker knows that the Internet is not a plaything, and one needs to know how to handle it properly to avoid falling victim to myriads of abusers. True?
True.
Even so, if you try to keep an eye on your own day-to-day online behavior, you will most probably find at least a dozen actions that could get you compromised.
Here are some of them:
1) The data breach problem
What is it?
The bigger and more precious any database in the world is, the more likely it is to fall prey of online thieves at one point or another. The reason why these breaches are so lucrative isn’t hard to fathom. There are people’s payment credentials, but also their personal health information, intellectual property and so much more. Once breached, these huge amounts of information can be abused directly or sold on the black market.
The problem isn’t only caused by all the hackers in the wild. There are also many insiders, that is who can simply point (with bad intentions or not) to the security hole for someone else to sneak in.
Stats
According to the IBM’s 2016 study, an average cost of a data breach for a company is $3.8 million. But there are many companies who suffer much more. The cost is often measured in hundreds of millions of dollars.
More than 7 billion data records have been lost or stolen since 2013, according to Breach Level Index. Only 4% of those were encrypted, so the thieves could make no use of them. To see for yourself how serious this is, do a simple thing and visit the aforementioned link again tomorrow, and you’ll see just how quickly this number grows.
Even giants suffer, which was proved more than once by none other than Yahoo. Back in 2013 more than 1 billion active accounts were hacked – including names, telephone numbers, DOBs, passwords and security questions. This problem was aggravated by the fact that users didn’t get to know they had been hacked until December 2016! That’s when Yahoo decided to disclose the breach, only to claim that it was sponsored by a government.
The list of big data companies that failed to protect their users’ data goes on. LinkedIn, Twitter, My Space, Tumblr were also victims of major breaches. No less than 167 million LinkedIn users’ credentials were stolen in 2012 and went for sale on the black market.
What am I to do?
It is utterly normal that the majority of people who have fallen victims to one or another data breach don’t even realise that until it gets too late.
If you want to see whether your email account is compromised, just go to the website HaveIBeenPwned and enter your address.
2) Phishing
What is it?
A click is cheap. Although we live in an illusion that we carefully choose the things we want and don’t want to click on, the truth is somewhat different. The creators of all of those annoying popups from the past know this all too well.
Phishing is a form of social engineering which abuses our natural curiosity and urge to click without thinking what this click is going to bring us. Although today we know better than to click the dancing cats and all those other colorful stuff that used to juggle on our screens in 1990’s and early 2000’s, phishing attacks haven’t ceased to exist. On the contrary, they continue to grow in scope and subtlety.
Phishing is actually a form of manipulation. The hacker pretends to be a trustworthy source. They may even clone a regular website or an email in order to appear harmless and legit. The point is to manipulate you into doing an action – enter sensitive info or click an attachment that contains and immediately executes malware.
More and more often, the attacks are precisely targeted to a company’s executive or another individual, in the form of an email that seems to be written by someone they know. Those attacks are known as spear phishing, or whaling.
Stats
Since most of phishing emails are being sent to corporations, there have been many mock attacks in order to see how likely are people to open and click email scams. According to the last year’s phishing stats published on Barkly’s blog, 30% of phishing emails get opened. Verizon’s 2016 Data Breach Investigation Report tells us, on the other hand, that 13% of the people they tested actually clicked on the phishing attachment in an email.
The last year’s Wombat’s State Of The Phish report found out that up to 85% of all the organisations have suffered phishing attacks in one form or another.
What am I to do?
Look at these examples of phishing emails which were received by Berkeley university students and staff. You will notice some patterns in phishing emails.
Check out the sender’s domain. Does it really fit into what they introduced themselves as? If there are links in the email, hover over them before actually clicking and pay attention to the destination which will appear in the down left-hand corner of your browser. If you’re in for a more detailed explanation as to what you should focus on, check out this Email Header Analysis article on GitHub.
And, of course, make your click hard to get.
3) Ransomware
What is it?
It is a form of malware which serves the attacker to hijack a database or a system, either to encrypt it and make it worthless for the user, or to lock it down so the user cannot access it – until he or she pays ransom. Of course, there is no guarantee that even paying the ransom will help the victim restore their possession.
What attackers rely on is the fact that people are ready to pay for gaining access to their data because legal fight would take time, and that could cause an even greater damage.
Ransomware is nearly 3 decades old. The first world-famous attack of the kind was the so-called AIDS Trojan, which was spread to the attendees of an AIDS conference in 1989. Once executed, it decrypted the file names and presented the user with an instruction to pay $189 in order to renew the licence.
Things got interested when they found that the virus’ creator, Dr. Joseph Popp, was no computer geek at all. He was an evolutionary biologist, who later defended himself that the money was intended to help an AIDS research.
Stats
Once again, email proves to be one of the weakest security spots, as 59% of all ransomware infections come through it, either through links or through attachments. This was one of the many results of Osterman Research.
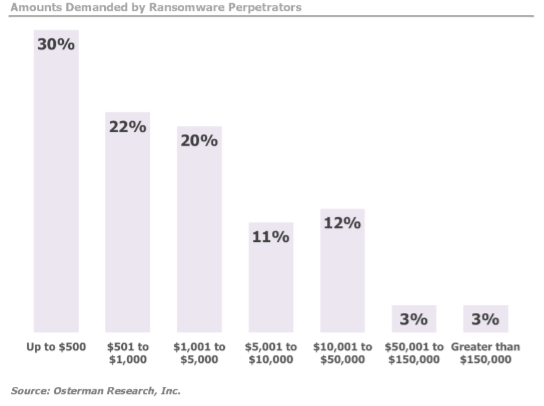
According to the Datto’s study, an average amount of money victims have to pay varies between $500-$2.000. However, one in each five companies paid more than $40.000. The same study claims that only a quarter of all the companies have actually reported ransomware attacks. And here is what the aforementioned Osterman Research has found about the sums.
IBM has found that even 70% of the business owners actually paid the ransom last year, even though FBI highly recommends not paying it, but appealing to the authorities for help.
In 2016, ransomware caused at least $1 billion worth of damage, making ransomware the most pervasive cyber threat since 2005.
What am I to do?
We won’t argue whether you should listen to FBI and report the ransomware attack, face downtime and wait for the investigation to finish.
It is best to always have your data backed up.
4) Defacement
What is it?
Cyber attackers don’t always intend to be criminals. Sometimes they can do it just for fun, or to nurture their omnipotent egos, or to employ their skills on a playground, practicing for a more serious stuff.
Website defacement looks just like that – by means of breaking into a server, the hacker can change the looks or content of the targeted website. It often happens via SQL (code) injections.
This kind of attack has made some of the most witty cases in history. Two years ago, a group of hackers who called themselves Lizard Squad took over Lenovo website for a few hours. During that time, Lenovo’s visitors were redirected to a slideshow of bored teenagers, apparently the hackers themselves.
This is one of many examples of hacktivism, which commonly happens through website defacement as a cyber form of graffiti. Cyber vandals use defacement to spread their political or other messages, or simply to warn the webmaster to improve security.
Stats
The most recent, and one of the most serious defacements in history happened two months ago, to 1.5 million WordPress users. The attackers defaced them by exploiting the REST API vulnerability, which is turned on by default in the 4.7 version of the software.
WordPress’ core contributors acted fast in patching this vulnerability, but they didn’t disclose it until a week later. They had the intention to buy some time for their users to update their software. Had they disclosed it immediately, it would have been a red alarm for all the hackers worldwide to instantly attack the security hole, before the users managed to update.
What am I to do?
The usual. Update whenever there is a new update. We can’t stress enough the importance of regular updating.
5) Brute force attacks
What is it?
Have you ever tried to guess someone’s password?
If yes, you know how hard it is to do it manually.
That’s why the attackers have made programs which try to guess users’ credentials by trying out as many combinations as possible. Many people use actual words in their password, which is why hackers have invented the so-called dictionary attacks.
There are also the so-called reversed brute force attacks, where a single password is tested against as many usernames as possible. Human nature is that predictable.
What about using numbers, special characters, combinations of lower and upper case? Yes, this does help. It really complicates things a bit. It isn’t impossible, but it may even take years to crack, depending on the length and variety.
Stats
Last October saw a great rise in brute-force attacks. Wordfence noted over 30.000 unique IPs performing attacks every day. The #1 country from which those IPs were attacking was Ukraine, with around 15% of all the attacks.
Speaking about the password length and complexity, here are some amazing stats about password cracking. It takes 11 hours to crack a 6-character password. For a 9-character password, a hacker would have to waste whooping 10 years.
When one takes a look at the most common passwords used in 2016, it is clear why brute-force attackers still don’t have much to worry about. The first one on the list in 123456, followed by 123456789 and qwerty. In the top 10 is also the password “password”. Without the quotes, of course.
Just how underestimated are the password-cracking attacks? Last year media reported that even Mark Zuckerberg’s social media accounts were breached by guessing the password – which was ‘dadada’. This is not the only mistake he made. He also used this password over multiple accounts. Bad way to go, Mark.
What am I to do?
Make your passwords at least 10 characters long. Mix uPpeR and LoweR case characters along with numbers and special characters. It would be best to actually pick words that represent nothing. Just in case you are wondering how long would it take to break your password, ask this page.
There are also password managers such as LastPass, whose basic features are available free of charge.
6) SEO poisoning (spamdexing)
What is it?
Search engine optimization (SEO) works so that the content which is the freshest, most relevant, popular and sought after comes first in the search engine results page (SERP).
The evil guys found they can manipulate search engines by using popular keywords to leverage the search engine rankings of malicious websites. This is, at least, what they did before Google introduced algorithms which are able to tell real websites from scam, high-quality content from click-bait etc.
Even then, the attackers didn’t give up. They usually use breaking news, big stories or holidays as a starting point. They may even clone a website or create a redirection to a phishing site. Google will sure discover and flag them in a while, but it won’t help users who have already bought into their story.
Stats
One of the most notable SEO poisoning cases in history was the 2010 Haiti Earthquake abuse. Those days many Internet users wanted to donate some money for those who were hit by the disaster. Cyber criminals took advantage of this and used these keywords to trick many people into donating money to false organizations.
A couple of days later, FBI warned U.S. citizens to beware of frauds and give money to trustworthy organizations only.
What am I to do?
Search engines today are pretty quick in discovering compromised or malware websites. Never click on a website has a warning that it may harm your computer. Also, be very careful with your sensitive information and charity donations, especially when big tragedies hit the world.
7) Backdoors
What is it?
You’ve probably heard the famous allegory of locking all the doors of your house, surrounding it with a 10-feet high wall made of stone… And leaving the windows open.
This is how backdoor attacks work. Typically, they are malware that enables an unauthorized entrance to a computer system, not by fighting or manipulating the security measures, but by bypassing them altogether. There are no smoking guns or traces that an evil act has been committed, which makes backdoors especially hard to discover.
Many backdoors were found in the pirated copies of commercial WordPress plugins. So, when a plugin costs money, either buy it, or find a free alternative (and there’s bound to be at least one).
Stats
The first world-famous backdoor (although not the first that ever existed) was Back Orifice, created in 1998. By abusing the then-current version of Microsoft Windows, it allowed remote administration of personal computers.
A good thing that sprang from this attack was that Windows got upgraded and improved in terms of security.
A bad thing – the hackers’ collective called themselves Cult of the Dead Cow. Imaginative folks, weren’t they?
8) Users
The hardest vulnerability to secure isn’t software, or anything like that.
According to many security researchers, among them Tony Perez, CEO of Sucuri, the biggest vulnerability, the most exploitable and the hardest to secure is – us.
They aren’t aware of the severity of the risks, or don’t pay enough attention to the protection, or just postpone it for tomorrow which never comes. They don’t allocate enough budget for security because it doesn’t produce profit. They don’t even update their software on a regular basis, even though it doesn’t cost anything.
This is why all the security threats we covered in this blog post can be cut down to this one, as the attackers know the people vulnerability all too well. They are aware of our bad habits, lack of knowledge, curiosity, negligence and carelessness.
Stats
According to Perez, only 35% of senior executives think it is vital to educate their employees about the dangers of data breaches.
60% of the same executives admit their employees don’t know a thing about security.
What am I to do?
If you are an executive or a high-level manager of a company, consider bringing forth the question of strengthening your security and educating your employees, including yourself.





Comments (1)
Kevin
You are right in pointing out the lack of motivation among many senior executives to educate their staff regarding the security issues and preventive measures that one needs to take. Pirated copies of plugins are a big NO!