Cyber Security Strategy: Who Needs It and Why
Making the headlines more and more often, cyber attacks have become part of our everyday existence. Equifax, Verizon, Shadow Brokers, WannaCry, NotPetya, Locky, Bad Rabbit – they are no longer funny names for scary new cyber threats no one knows quite enough about, but cautionary tales about companies failing to monitor and protect their networks as well as users neglecting basic security hygiene.
But first, how to know your company is in grave danger out there?
This should come as no surprise, but bad guys tend to follow the money or power. 8 out of 9 types of cyber criminals target the most affluent industries – financial, military, IT, energy, NGOs, legal, retail, healthcare:
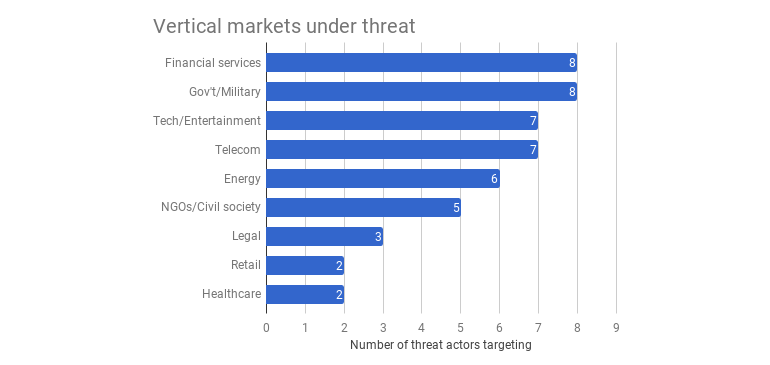
The good thing about a cyber security strategy is the fact that it demands a unified approach to keeping the company assets safe in cyberspace, since research suggest that perspectives can differ greatly between CEOs and Technical Officer, thus weakening enterprise cyber security. CEOs tend to be focused on malware, creating misalignment within the C-suite, which results in undue risk exposure and prevents organizations from effectively stopping breaches. On the other hand, Technical Officers (CIOs, CTOs and CISOs) on the front lines of cyber security point to identity breaches — including privileged user identity attacks and default, stolen or weak passwords – as the biggest threat, not malware. As a result, cybersecurity strategies, project priorities, and budget allocations don’t always match up with the primary threats nor prepare companies to stop most breaches.
The research — a survey of 800 enterprise executives including CEOs, Technical Officers, and CFOs – highlights that:
- 62% of CEOs cite malware as the primary threat to cybersecurity, compared with only 35% of Technical Officers
- Only 8% of all executives stated that anti-malware endpoint security would have prevented the “significant breaches with serious consequences” that they experienced
- 68% of executives whose companies experienced significant breaches indicate it would most likely have been prevented by either privileged user identity and access management or user identity assurance.
A coherent cyber security strategy requires a template or framework containing all of the important components – those that are most applicable to your company’s particular circumstances, leading to a process that should point you towards the most appropriate security measures. Here are some of them:
- Governance, Compliance and Organization
- Data Protection
- Security Risk Management
- Identity and Access Management
- Incident Response
- Third-Party/Vendor Management
- Host and Endpoint Protection
- Application, Database and Mobile Protection
- Network, Cloud and Data Center Protection
- Security Awareness and Training.
Currently, the most commonly cited focus areas across the aforementioned industries are data protection and incident response, closely followed by identity and access management:
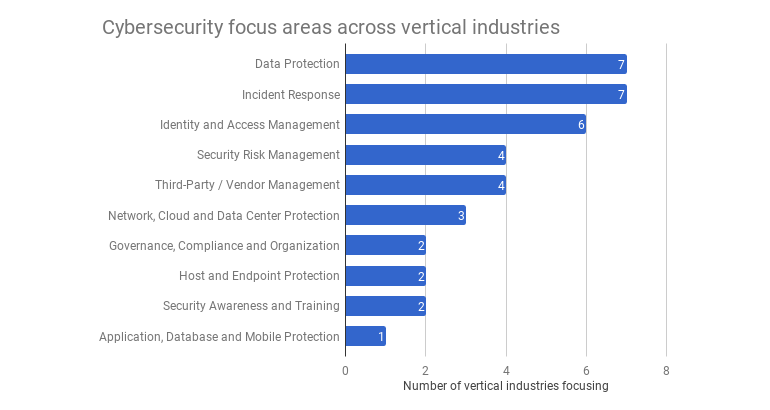
Furthermore, what should you do to protect your business in cyberspace?
You cannot lock down the company IT systems, but you shouldn’t wait to lay down and wait for the attackers to find you. Once discovered vulnerabilities, they WILL be exploited, and that can cost you a lot, maybe even make you close your doors eventually. Moreover, here are the 7 devastating effects cyber attacks can have on your business:
- Electronic data damage or loss
- Income loss
- Extortion expenses
- Network security and privacy lawsuits
- Notification expenses
- Renewal expenses
- Reputational damage.
These can all have serious long-term consequences on the way you run your business – even if you get a business to run when the dust settles. That is why you need a game plan which will allow you to hit the ground running and be ready when they come for you.
In our previous blog post, we have stressed the importance of a threat-led cyber security strategy, one that has identified all the vulnerabilities of your IT systems, all the ways they can be targeted, as well as how to defend against them. To create a baseline for such a strategy, you need to perform a cyber threat and risk analysis so that you can get a picture about what is currently happening in cyberspace and which methods the attackers are using.
- The 1st step in the process is to establish the likely TARGETS OF A CYBER ATTACK when it comes to your business. Bear in mind that sophisticated cyber attackers infiltrate your network with a specific intent – to gain access to the data only you have that are especially interesting to them.
- The 2nd step is to pinpoint the THREAT ACTORS, or cyber criminals, nation states, hacktivists and insiders who could target your industry, sector and business. They should be ranked in order according to their motivation, capability and likelihood of them targeting your company, as well as the methods they use, assigning each a value to determine their overall threat to it.
- And the 3rd step is to put in place A MECHANISM OF CONTROLS – to detect, prevent and respond to possible cyber threats. (To see how to protect your small business from cyber attacks in 6 steps, take a look at our infographic.)
Creating a detailed analysis of the threat landscape for a company’s particular business sector should lead to the adoption of an appropriate framework within which to develop a security policy – suggesting the best combination of security measures to deploy. Not only that, but policies must be revisited and updated as the threat landscape evolves.
If you find yourself doubting you can successfully create and implement a cyber security strategy, you can trust Awontis to keep you safe. We have over 275 clients who are more than satisfied with our services. On more than 1500 websites we actively monitor, nearly 55.000 security threats were successfully prevented using our solution. The websites under our protection are watched 24/7 for threats and updates, allowing the businesses they represent to thrive. Finally, the already compromised websites are fixed by being thoroughly cleaned of malicious content and protected from future threats.
Since no security threat can be removed permanently on the Internet, we will keep your defense line firm and evolving with security practices to keep you safe.

